How to Upload Projects on Github Without Security Breaches
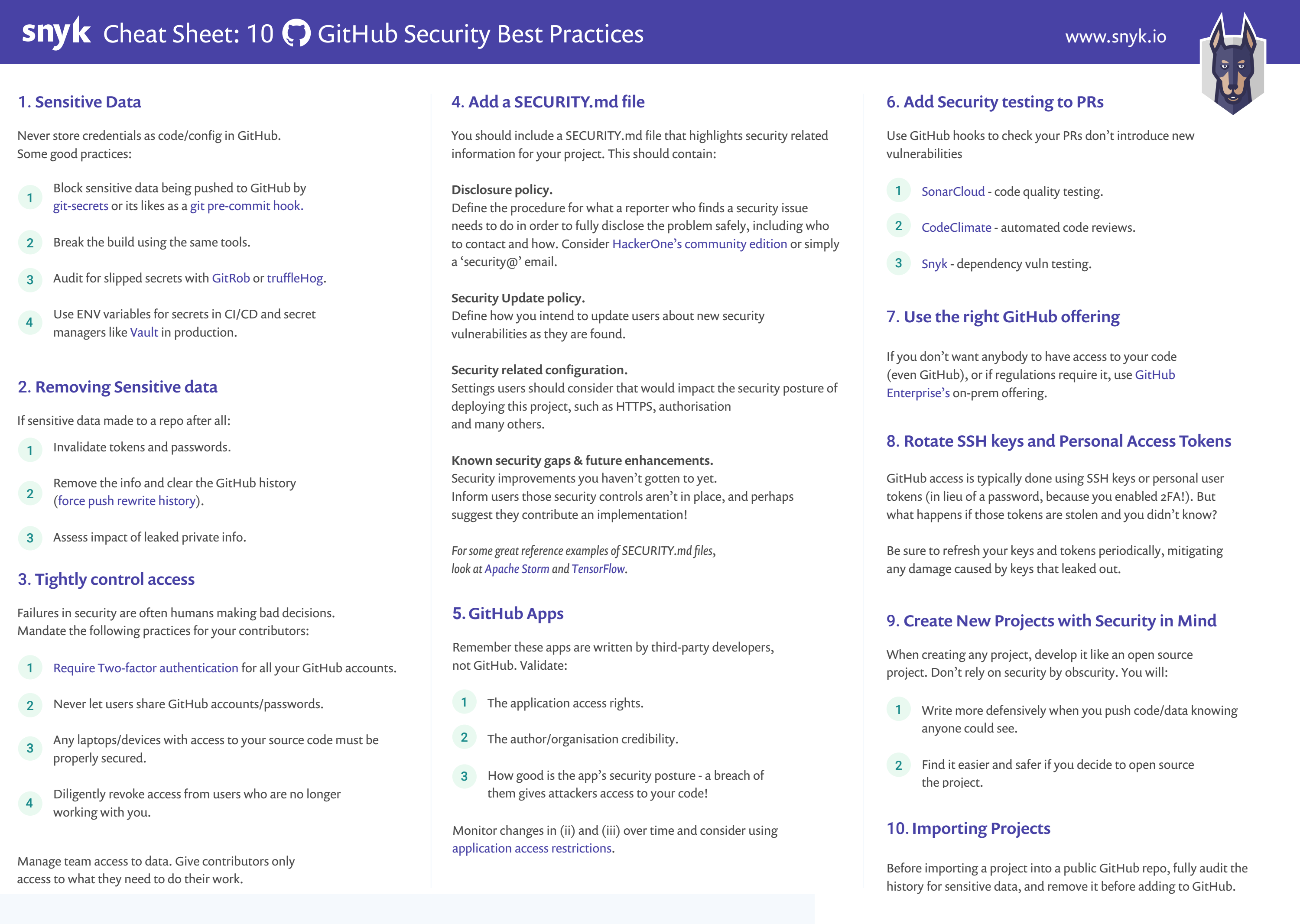
In the 2d installment of our cheat sail series, we're going to cover how you can be more secure as a GitHub user or contributor. Much of it is specific to GitHub best practices, merely there's besides general advice in both the cheat sheet and this blog that is applicative to other source code repositories. Yous can download the GitHub Security Crook Canvas here. In example you missed our start cheat sheet on the dos and don'ts of Coffee type inference introduced in Java 10, make sure you check that out as well.
So allow'southward get started with our listing of 10 GitHub security best practices, starting with the classic error of people adding their passwords into their GitHub repositories!
i. Never store credentials as lawmaking/config in GitHub.
A quick search on GitHub shows how widespread the problem of storing passwords in repositories really is. The 350,000 commits returned from this simple search does not cover those who were not so obvious with their commit messages, or those who tried to cover their tracks past removing their history. All in all, this is a big problem that doesn't show real signs of being fixed. That said, at that place are some GitHub best practices you tin follow to foreclose sensitive data being added into your repository.
In that location are a bunch of great tools available, like git-secrets, that can statically analyse your commits, via a pre-commit Git Hook to ensure you're not trying to push whatever passwords or sensitive information into your GitHub repository. Commits will be rejected if the tool matches any configured regular expression patterns that are designed to observe sensitive information. It may dull downward pushes a tiny bit, but it's well worth it.
You can also utilise tools similar git-secrets in your CI and CD pipelines to actively interruption builds when sensitive information is plant in code or a config file. Having team-broad rules that forbid this from happening is a great fashion to police bad actions in the existing developer workflow. A preferred way to hold or pass sensitive information is through the environment variables of the called CI/CD pipeline tools you are using, such as Jenkins or TeamCity. You tin also use a tool like Vault to assist with your secret management in production. Lastly, consider using an identity and user management tool chain, like Keycloak (currently maintained past a number of developers in Red Lid) every bit well as others.
In that location are many means to avoid putting credentials into your repository in the starting time place, and you should try to implement as many as you lot tin can, simply there'southward always the chance some sensitive data may sneak in. You should besides consider regular auditing of your repos, making employ of tools like GitRob or truffleHog, both of which scan through your codebase, searching for sensitive data via design matching.
2. Remove Sensitive data in your files and GitHub history
If you lot find sensitive data in your GitHub repository, y'all need to do a number of things to recover. First of all you'll demand to invalidate the tokens and passwords that were once public. One time a undercover is public on the net, you should assume it's in the hands of attackers and react appropriately.
Of course, you'll also demand to remove the sensitive data from your repository, but don't forget that GitHub is very skillful at keeping a total history of all your commits. This includes changelogs that will listing your sensitive information. Information technology'south important yous articulate your GitHub history when you lot remove sensitive data from a repo. For more info, meet purging files from your repository's history.
Test your GitHub repo for vulnerabilities
Find and prepare vulnerabilities in your repository for free
three. Tightly Control Access
Here in the UK, when it gets really, really hot (read as, mildly warm) us Brits tend to open all the windows in the business firm to make certain that it doesn't turn into a sauna. However when we leave our houses, we'll double lock the front door, ofttimes leaving many of the windows partially open to keep the airflow moving. Of course this makes no sense, every bit anyone wanting to break in won't try to break in through the front door! They'll look for an easier way in, possibly by climbing through one of the conveniently opened windows. We often take the same arroyo to securing our applications. We tin focus very hard on the more complex assault vectors, but fail miserably against some of the simplest.
For instance, information technology merely takes one developer to leave their password on a viscid note, hanging off their monitor for an attacker to gain access. Nosotros must ensure our basic settings and practices, both on the GitHub platform likewise equally in full general, are adhered to. Mandate the following basic practices for your contributors:
- Require two-factor-hallmark on every contributor'due south GitHub account.
- Never let users share GitHub accounts/passwords.
- Any laptops/devices with access to your source code must be properly secured.
- Repository administrators should manage team access to data. Only give contributors admission to the data they need to do their work.
- GitHub accounts are often personal ones, and do non naturally disappear when users get out the company. Brand sure you diligently revoke access from users who are no longer working with you.
four. Add a SECURITY.md file
It'due south natural for most projection owners and maintainers to add a README.md for their repository. In fact, these days information technology'southward quite frowned upon if one is missing. Likewise, it's becoming increasingly mutual to add a SECURITY.md file that highlights security related information for your projection. Non but does information technology give users the important security information they need, but it also forces the maintainers to recollect nearly how they should deal with security disclosures, updates and general security practices.
Here's a loftier level overview of some of the suggested topics that you should cover in the SECURITY.md file:
Disclosure policy.
The 2020 Snyk State of Open up Source Security written report shows that only 21% of respondents check for responsible disclosure policy. Meanwhile it is disquisitional to define the procedure of how an consequence reporter can fully disclose security issues responsibly. This should include who to contact and how. This is extremely important as it allows you to gain important feedback from your users.
People are lazy in general and if there's no piece of cake of well divers manner of doing something, it'due south easy for us to not carp doing it at all. Others may log the existence of a vulnerability as an open up issue, inadvertently making the world enlightened of information technology before a set is available. Make sure yous requite your users all the direction they demand to give the correct data to project maintainers when bug are constitute.
Security Update policy.
Software vulnerabilities are discovered every single day. When a vulnerability is institute in your application or library, yous accept a responsibleness to your users to tell them most it. They could exist using your open source code in production on critical systems. You demand to take a well defined process to share the relevant data with them, including the severity of the vulnerability, the risk information technology brings, and how to move to a stock-still version of your code.
Define this procedure upfront so that the information is pushed to your users, allowing them to exist updated as early on equally possible about new security vulnerabilities as they are found and fixed.
In 2020 Snyk discovered a prototype pollution in Lodash. At the fourth dimension, the popular npm library was used by four.35 million projects on GitHub alone. The project had just shy of 40k GitHub project stars, and the library had been downloaded over 80 million times each month. The squad proactively opened thousands of automatic set up pull requests for its users to remediate the vulnerability.
A SECURITY.dr. file is a good home for such info on the repo, and if y'all have a website, consider an independent folio for it – see Express.js's security page equally an case.
The security considerations of your project get beyond your code alone. Users will likely need to configure your projection and create settings in order for it to work as they demand in their environs. You should provide your users with suggested settings to consider that volition harden their security posture when deploying this project.
Examples include turning on HTTPS, calculation an authorisation layer and of course replacing default passwords (guidance many MongoDB users wish they've gotten). Remember that users typically have a fairly low understanding of security, so any advice you lot tin can pass on volition help them greatly.
Known security gaps & time to come enhancements.
Very rarely are projects in such a state that all the security improvements you lot want to make have been implemented. It's important to inform users of the security controls that aren't currently in place. Your users deserve to know the total story so they tin make informed decisions nigh how they use your projection. Who knows – y'all may fifty-fifty get contributions from your users of a security command implementation on the listing!
There's a tradeoff betwixt giving your users the information they demand to secure their surroundings versus enabling an assaulter with suggested set on routes. Always consider how the information you share could be used past both parties.
Skilful examples of SECURITY.md files in the wild can be seen in the Apache Tempest and TensorFlow repositories.
5. Validate your GitHub Applications Carefully
All practiced platforms can be extended, and GitHub with its application marketplace is no exception. Applications are written past organisations and third party developers, and then keep this in mind when adding them to your repository. Consider the following when selecting and installing GitHub applications:
- Don't give applications more admission rights than they demand.
- Question why an application requires the level of admission it asks for, and think virtually the damage information technology might cause with that level of access.
- Validate that the writer or organisation behind the application are legitimate and have credibility before giving them admission to your repositories, the same every bit you would bringing in a new committer.
Y'all're only as secure as your weakest link, so if an application yous're giving access to has a poor security posture, a breach of their code will requite attackers access to your lawmaking – one of your most sensitive assets.
Lastly, make certain yous monitor or audit your applications and their contributors at regular intervals to ensure you still need them, all the same trust them, and all the same deem them worthy of the access they require.
6. Add Security Testing to PRs
GitHub has a powerful event driven Git Hook framework that allows you to send HTTP POST requests to a service of your choice when events are fired. In that location are a vast number of events you can cull to act upon, simply one of the most useful for testing your incremental code changes is the pull_request event. In that location are many static code assay tools that support Git Hooks such that when a PR is created, an HTTP POST is fired to prompt them to examination your latest updates. This is a groovy betoken in fourth dimension to ensure that code and config changes being made are aligned with your security expectations.
Let'due south use Snyk equally an case (a fleck of a shameless plug, but a practiced example even so). Snyk statically analyzes your repo to find vulnerable dependencies yous may be using and helps you fix them. You tin can test your repos through Snyk'south UI to discover issues, but also to go along users from calculation new vulnerable libraries by testing pull requests and failing the exam if a new vulnerability was introduced.
Beyond the convenient integration into GitHub, pull requests are better than "breaking the build" in the fact they don't accept to cake a merge (in fact, they're informational past default), and their ability to test your changes, not but the result (east.yard. fail only if y'all introduced a vulnerable library, not if in that location was one there already).
In addition to Snyk, you should also consider using SonarCloud or CodeClimate to perform automatic security code reviews.
Test your pull requests for vulnerabilities
Detect and gear up vulnerabilities earlier you merge, so you can ship securely
7. Use the Correct GitHub Offering for your Security Needs
Depending on your project or organisational regulations, you lot may be restricted to software that tin can only run locally. Or perchance the restrictions are on where your source code is stored or which other organisations can have access to information technology. This is a common restriction for fiscal institutions, regime departments or other tightly regulated industries. Even so this doesn't mean that you lot tin't use GitHub!
Take a wait at the fully on-prem GitHub Enterprise offering, which allows you to fully host GitHub repositories within your organisation. This ways your can be disconnected from the internet and still have internal access to your projects inside your GitHub Enterprise repositories. Not even GitHub have admission to your codebase!
viii. Rotate SSH keys and Personal Access Tokens
GitHub access is typically washed using SSH keys or personal user tokens (in lieu of a password, because you enabled 2FA!). Only what happens if those tokens are stolen and you didn't know? Be sure to refresh your keys and tokens periodically, mitigating whatever impairment caused by keys that leaked out.
ix. Create New Projects with Security in Mind
When creating a new project, developers are ofttimes happy to hack effectually and accept short cuts just to get an application up and running. This might pb to developers becoming sloppy with sensitive information like passwords which might exist hard coded, or stored locally in config, similar a properties file. Less blatant security secrets include relying on a secret algorithm to authorise input, or exposing how y'all seed random numbers It's a good practice, even for a closed source project, to develop it with an open source mindset. You'll more likely write better code that is more secure if y'all consider you're writing code that others will run across and potentially exploit.
In addition, if you lot ever exercise recollect that you'll want to open up source the code it volition exist a lot easier and safer as you were already thinking in the more secure open up mindset, so there's less change yous'll miss a password or central that you hid in the code.
ten. Inspect whatsoever Code you Import into GitHub
This leads u.s.a. nicely into what y'all need to exercise when yous import projects or large chunks of code into GitHub. Source code that y'all import into GitHub may have existed for months or years, and maybe been developed in a airtight source repository. This tin pb to many of the once reasonable assumptions fabricated in a closed source environment now being invalid. Always ensure you exercise a complete audit earlier you lot import anything into GitHub. This might be a lilliputian exercise for smaller projects, but once your codebase reaches a certain size, it can take teams many weeks or months to fully audit, update and pull in to an open source repository.
For further reading on GitHub security best practices, make certain you also read the GitHub security documentation and the GitHub business security site for additional features such as external auth/SAML support. And if y'all haven't done so notwithstanding, make sure y'all download the cheat sheet now and pin it up, so your future decisions are secure decisions!
Secure your GitHub repo for free
Find vulnerabilities in your repository and ready apace with automated fix pull requests
Source: https://snyk.io/blog/ten-git-hub-security-best-practices/
0 Response to "How to Upload Projects on Github Without Security Breaches"
Post a Comment